How to remove a security tag from clothing
2008-04-13

Some time ago we bought a piece of clothing at an amusement park. When we got home we discovered that a security tag was still attached to it. Needless to say we were not going back to the amusement park just to have it removed so I decided to remove it myself and find out how such a tag actually works.
Disclaimer: These instructions were posted here to describe the working of the security tag, I don't condone stealing, use at your own risk, etc, etc.
Opening the tag

The trick is to saw the top of the tag off as illustrated here. It seems that most similar tags are weakest at the top and can be broken in this way.
I used a regular fine saw. The plastic was softer than I had expected it to be and it was open in just a few saws.

This exposes a softer plastic container that holds the actual mechanism to hold the pin in place.

After cutting the soft plastic (with a fine saw or knife) the contents of the tag come out and expose the mechanism. At this point the pin can be removed and the piece of clothing is freed from the security tag's clutches.
Having a look inside

Taking the whole thing apart clearly shows the plastic container, a bucket-like container, three balls that press against the pin, an element to keep the balls in place and a spring to apply pressure.

If we take the tag itself apart even further and cut it open it exposes an antenna that is used to trigger the alarm when you leave the store (which was probably broken in this tag).
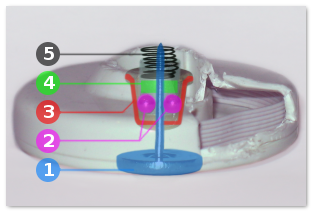
Summarising, the mechanism basically consists of a pin (1)
that is secured by a couple of balls (2)
that press against the pin because they are in a bucket (3).
The balls are kept in place by the guide (4)
which also assures that the spring (5) can
apply pressure.
The plastic around it is mostly to keep everything in place and to
make it harder to attack the tag by cutting the pin.
The unlocking presumably works by using a magnet to pull the balls up, lowering the tension on the pin and making it easy to remove. The balls which were slightly magnetic and were sticking together confirm this assumption.
Conclusions/references
The top was clearly the weakest point of this tag. It seems that most similar security tags are also vulnerable at the top. This could be easily protected by making the plastic container that holds the bucket something that is harder to cut.